Incident Response & Incident Response Planning
History tells us it is not a matter of if but when we will have a cyber related incident. DMA incident response service provides seasoned security consultants to investigate and report in real time on who did what when, how and how to deal with it.
We help organisations plan for incident prevention, document the response process and enable staff to be confident of their immediate action in the detection of an incident.
The DMA health check may be a good start, if you are beyond a start and ready to document the entire process to be prepared, please call us to arrange a time for a consultant to visit you and advise how we do it.
DMA Quick Tip: Sort out logging – who what where when and how to enable incident response to occur.
DMA incident response and incident response planning help decide who is going to what and how, preventing further ex filtration, penetration or disruption to your systems.
Safety net & build wealth
You can transform your business to a revenue-producing asset that lets you work as much or as little as you want.
Incident response & incident response planning
Our clients are often surprised by the possibilities we present to them; by thinking outside the box we present exciting new ventures:
- Do we the right people process and technology to deal with an incident?
- Do we have a plan?
- What types of incidents could effect us and do we have an IA plan (Immediate Action Plan)
- Hone sharp leadership skills to manage the team, table top exercises for IR
- Cut expenses without sacrificing quality
- Automate responses
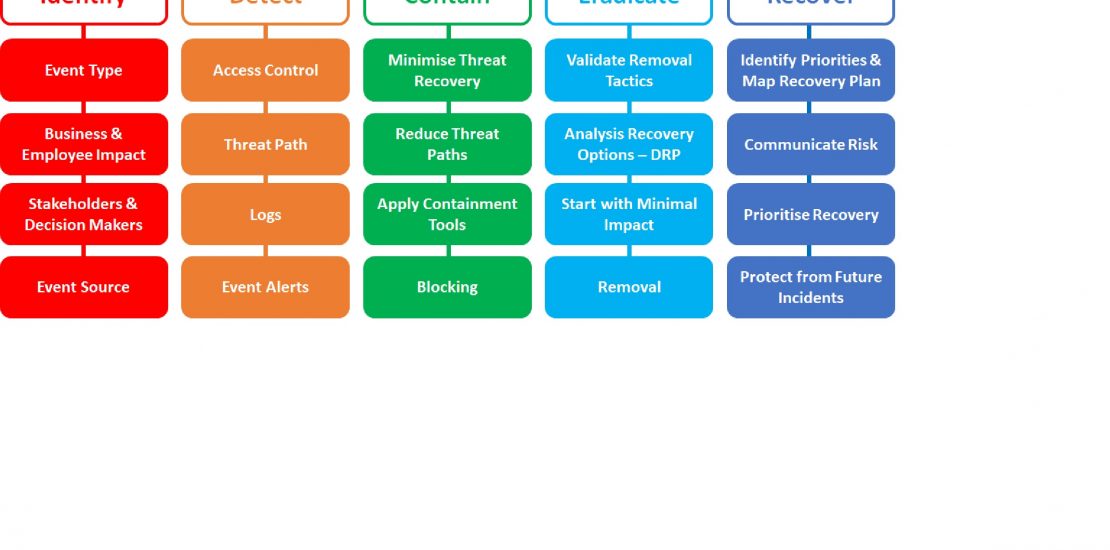
How do we do incident response well?
6 P’s = Prior Planning & Preparation Promotes Positive Performance
IR Done well requires business input, planning, technology and people to deliver on discovery and the IR or OMG Plan. DMA help document what do prior to an incident, what to do upon discovery of an incident and who does what when and how from discovery to lessons learnt post fix. This includes;
- what the CEO is going to say to clients, suppliers, staff and stakeholders via the multiple communication mediums
- what the technology team is going to do and how, depending on the type of incident
- how do we get our data back, what is our RPO and RTO
- what are our people process and technology in place for prevention and detection, and then management and resolution
Document why we need a plan, what is in scope to protect and respond to if required, by when, by who and what with. The Army does very well at teaching IA’s (Immediate Actions). Effective Incident Response is achieved by having effective immediate actions document, tested and practiced in order to deliver on business RPO and RTO requirements, regardless of scenario.
Incident Response starts with a board directive that the organisation should have the capacity to response to any type of incident incident if and when required. The response should be measured, achieve defined outcomes, (usually RPO and RTO, damage control) tested and practiced.
Organisations should not underestimate the stress and pressure management and staff will endure when mid incident. The long term damage of not planning how to deal with an incident will be measured not just in financial impact. It is critical for holistic organisational intelligence and sustainability to undertake incident response planning extremely well. Please call for more information and a 1 hour Incident Response planning workshop .
Incident Response Engagement Model
A strong IR plan requires going beyond intuition and experience, and supporting your plan with fact-based testing and learning. Response teams need to have confidence in your understanding of the environment, so don’t let yourself down by skimping on research & testing. What we do to help achieve confidence:
- Monitoring of multiple sources – Logs from Application and Infrastructure stacks
- Correlation Rules – Company and Industry Research
- Threat Hunting – Malicious code, activity, ‘not normal’
- Digital Forensics – who what where and how, (maybe why)
- Security Posture Guide – Are we CMMI Level 3, perhaps close?
- Lateral Movement Identification – what can we see and how?
- How to prevent an attack – best forms of defence
- Vital Assets – what are we defending and how?

